
PROCESSING. PLEASE WAIT...

White Paper: LEGIC
Anthony Fitze, Carl Fenger, LEGIC Identsystems
An Overview of LEGIC for the complete version - Click Download.
In industrial environments, mass deployment of sensors and the ability to securely collect and process data from fixed and mobile assets increases efficiency and enables better business decisions. It makes it easier to streamline processes, reduce errors, support auditing and enforce quality control.
The common denominator: Trust
Connecting sensors to the internet is not enough. Improving processes via the “Industrial Internet of Things (IIoT)” depends on a common denominator: Trust. If users, sensors and their interactions cannot be trusted, the results can be costly and even catastrophic, especially where volatile assets and safety are involved, which is often the case.
The Three Pillars of Trust in the IIoT
Being able to trust in IIoT data relies on linking authenticated users with trusted sensors/objects so that their interactions are reliable, transparent and accountable. Accomplishing this relies on three principles:
1. Accountability: users must be authenticated and accountable before gaining access to sensors or infrastructure. Access permissions must be assigned based on roles, training and authorizations plus context-based criteria such as time and location. Permissions must be autonomously enforced, both online and offline, to minimize human error and support 24/7 operation. All activities must be transparent and auditable.
2. Security: equipment must be configured and accessed by authorized users onsite. As sensors at the edge are the most vulnerable component of an IIoT system, physical hardware-level security must be implemented in the form of an embedded Secure Element for hosting of cryptographic keys and user permissions.
3. Transparency: all interactions between users and devices must be trustable, auditable and transparent to authenticated users. At the same time, they must not be visible to, nor subject to interception by unauthorized parties either at the sensor, along local area networks, air interfaces or over the public internet.
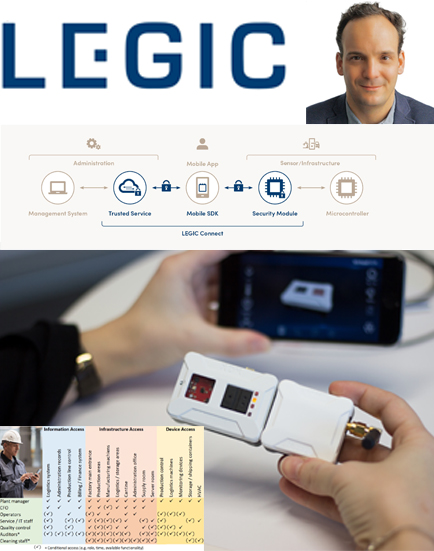
Security by Design: LEGIC Connect mobile credentialing platform for IIoT system users
LEGIC Connect is a mobile credentialing platform that securely distributes mobile credentials or other data to registered iOS or Android smartphones or tablets anytime, anywhere and instantly at the touch of a button.
The system provides a globally available, AES encrypted, end-to-end mobile credentialing service that is the backbone of establishing trust and accountability in user/sensor /infrastructure interactions. The system can be easily integrated into existing infrastructure and applications, enabling service operators to manage user permissions and send/receive data securely from/to smartphones and sensors. For details see www.legic.com/connect


 2025 All Rights Reserved | by: www.ciowhitepapersreview.com
2025 All Rights Reserved | by: www.ciowhitepapersreview.com